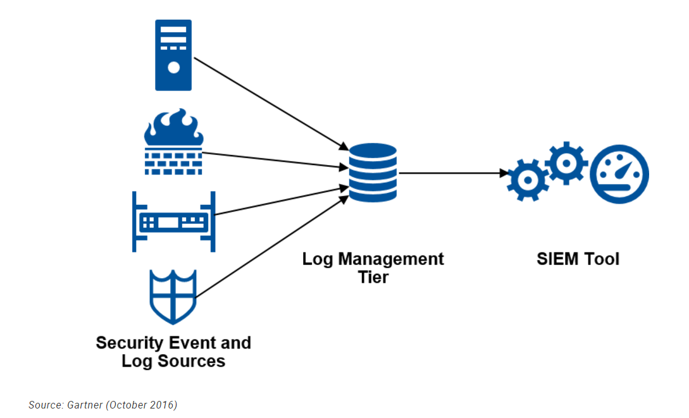
The importance of logs isn’t in the logging itself. Instead, it’s the analysis of these logs is what provides value. SIEM, though, is a significant step beyond log management. Detection is the most critical and indispensable part of a SIEM otherwise we use log Management.
SIEM is about looking at what’s happening on your network through a larger lens than can be provided via any one security control or information source.
The power of correlation.
With only the logs, all an analyst sees is: “Bob authenticated from a foreign country”. The Analyst needs this information to make a reasoned assessment of any security alert involving this authentication. The true value of logs is in correlation to get actionable information.
“if you are spending 80 percent of your time within a SIEM tool doing alert review and analysis, then you are on the right track. If you are an organization that is instead focusing heavily on collecting more data sources, applying patches, or running compliance reports, then your SIEM implementation may not be tactical.” JUSTIN HENDERSON — https://cyber-defense.sans.org/blog/2018/10/24/your-siem-questions-answered
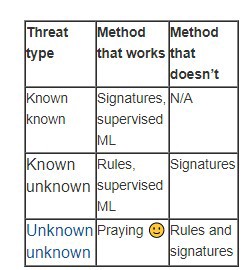
Rule based or ML based, a good SIEM must have a strong correlation capability.