Organizations still get hit with malware and ransomware in spite of that fact that antivirus and firewall solutions are in place. For this reason, a layered security approach will be more effective to catch malware infections before they start running. We will show you how LOGTITAN SIEM can effectively identify and stop malware on the network.
Use Case: Malware on the Network
- Unusual network traffic spikes to and from sources
- Endpoints with about 8 malware threats
- Significant Network Slow down observed
- User complained INTERNET is too slow in hostels
For this use case, we will use:
1- Firewall logs,
2- Endpoint security logs
3- Threat Intelligence Feeds
With LOGTITAN SIEM, security admins have two detection options.
- Correlation
- Log investigation.
Correlation
Use Case steps:
1- Collect endpoints with malware threats.
2- Calculate the total traffic between devices.
3- Check if one of those devices has eight malware threats within the last 24 hours.
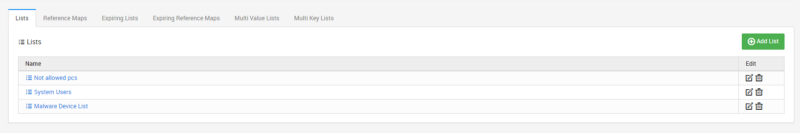
Malware Device List
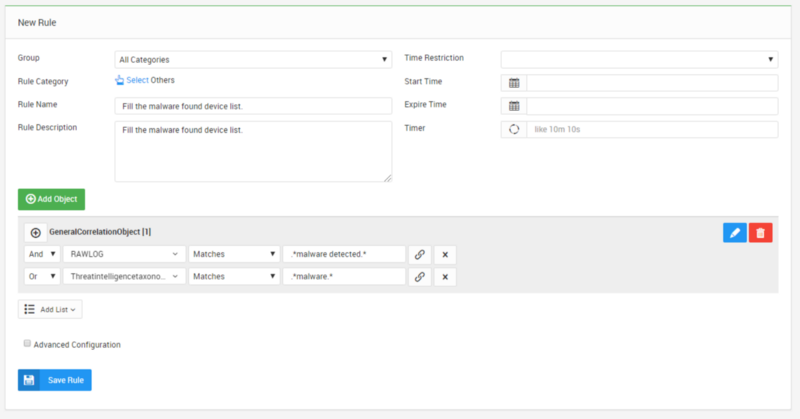
Rule Part 1:Collect the malware found device list
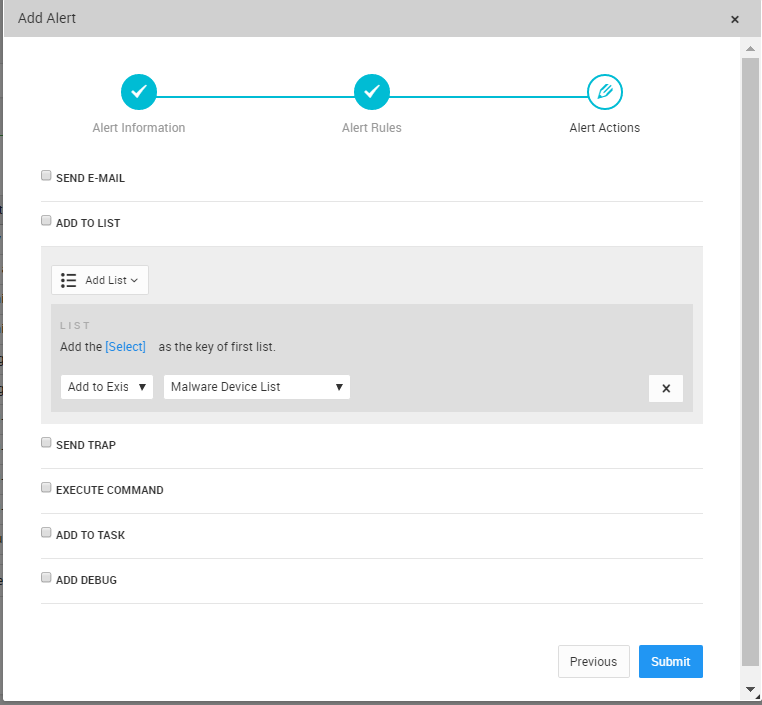
Rule Part 1.1: Fill the malware found device list
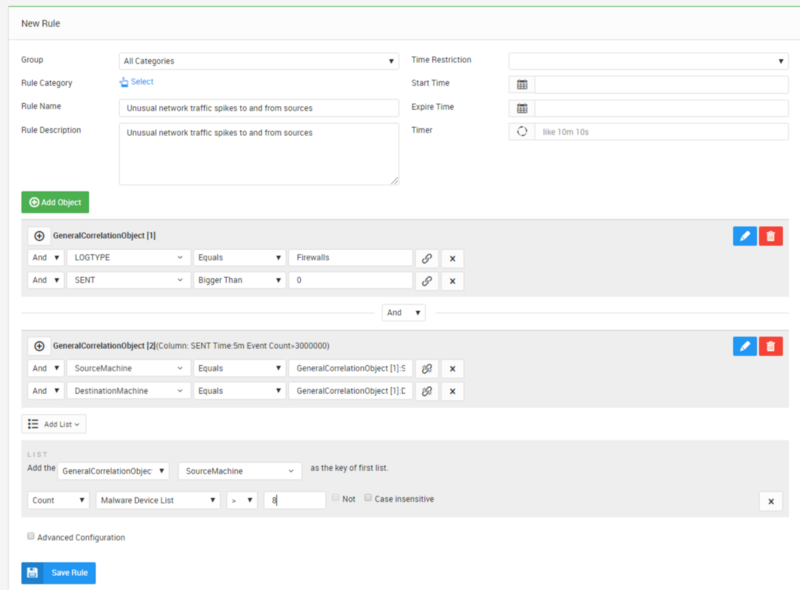
Rule Part 2: Unusual network traffic spikes to and from sources and endpoints with about 8 malware threats
Rule Description:
The first part of the rule collects log from endpoint security devices or Threat Intelligence Feeds and fill the “Malware Device List”
The second part of the rule checks if there is more than 300 MB upload and 8 malware threats
Log Investigation
The first part of the investigation is to find traffic peaks.
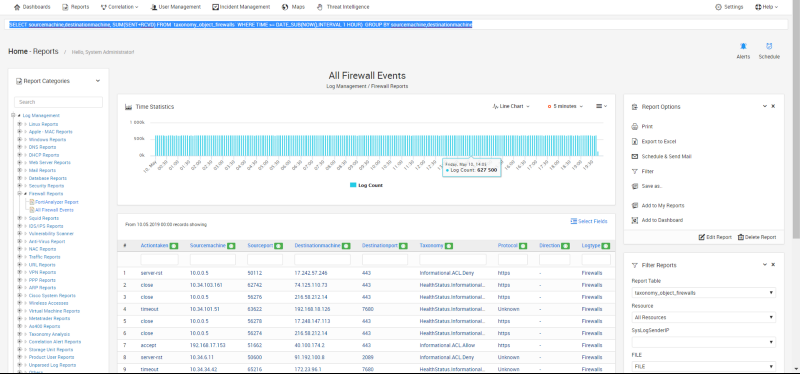
Firewall Logs
Within firewall logs, look for peak traffic.
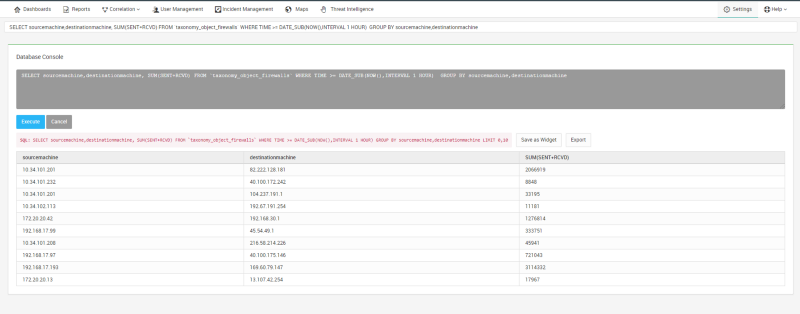
Total traffic within 1 hour from SourceMachine to DestinationMachine
The second part of the investigation is to look for eight or more malware threats within endpoint logs.
![]()
