Identify events that matter most
In a volatile and fast changing threat landscape, security information and event management (SIEM) plays a vital role in keeping your business productive by defending your IT infrastructure against malicious attacks and protecting vital business and customer data.
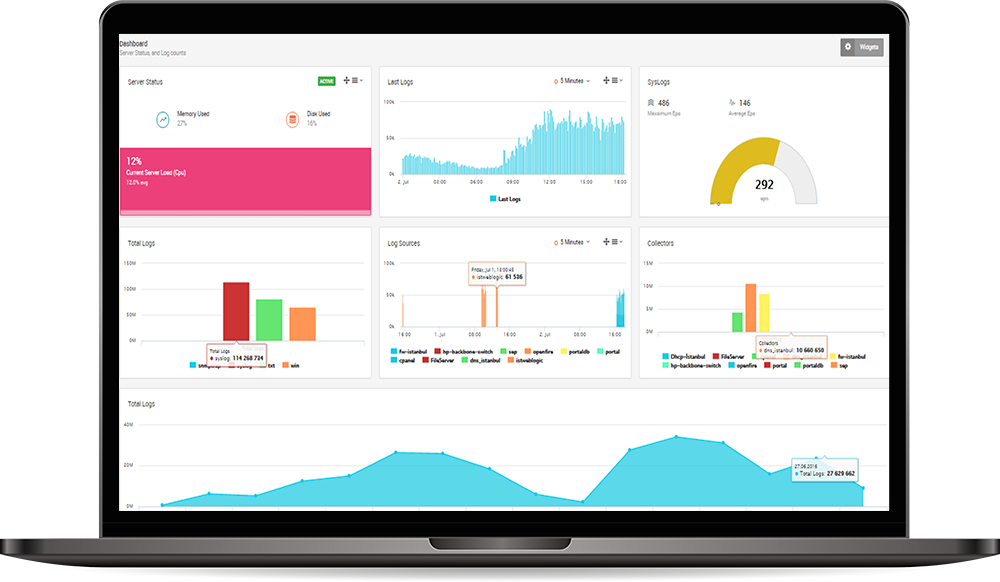
Forensic capabilities — LOGTITAN offers forensic analysis capabilities from the event source. Easily aggregate and search logs within a single platform.
Dashboards — LOGTITAN provides the ability to easily create dashboards and reports.
Threat intelligence — LOGTITAN has the ability to integrate with internal/external intelligence sources.
Performance — The performance analyses of SIEM products are very important in terms of evaluation. The running performance of SIEM products, the resources which they require (CPU, RAM, DISK) and how they will show performance in the EPS value needed is very important. LogTitan can handle 10000 EPS with hundreds of rules enabled with All-in-One installation.
Compliance Reporting — LOGTITAN has more than 1400 predefined reports and very easy & fast reporting infrastructure.
Incident response — LOGTITAN analyzes event log data for potential security incidents and response in real-time.
Machine Learning — LOGTITAN improves its own accuracy through machine learning and deep learning.
Live log search capability — The latest study by the Ponemon Institute on behalf of IBM found that the average time required to identify a data breach is currently 197 days. So having logs under hands at least 197 days is a good plus and makes everything easy for detection and forensic analysis. It is achieved by live search capability. Disk usage for live search is the most critical parameter. Logtitan is the best on the market
ML models used by LOGTITAN
- Detecting tools used by cyber criminals
- Hunting critical process masquerade
- Hunting malware and viruses by detecting random strings
- Domain generation algorithm (DGA) detection
- Profiling user and entity behavior
Start Your Free Trial Now!
Fill form below and we will send you your trial info.