We will show you how LOGTITAN can effectively identify and stop malware on the host.
Use case: Malware Dropped to a HOST
- URL link over an email received
- The user clicked on it and provided the required information
- The user received a LOG-IN notification from a system, he/she was authorized to access
- The user reported that she did not log in
For this use case, we will use:
- Mail gateway or sandbox logs which have the URL part of the mail message,
- Proxy or UTM logs
- Authentication logs from servers, databases, network devices, etc..
With LOGTITAN SIEM, security admins have two detection options.
- Correlation
- Log investigation.
Use Case steps:
- Get URL link from mail gateway log. Ex Fortisandbox,
- Check if there is a request to this URL from proxy logs,
- Check if there is an authentication within 15 minutes with this user account.
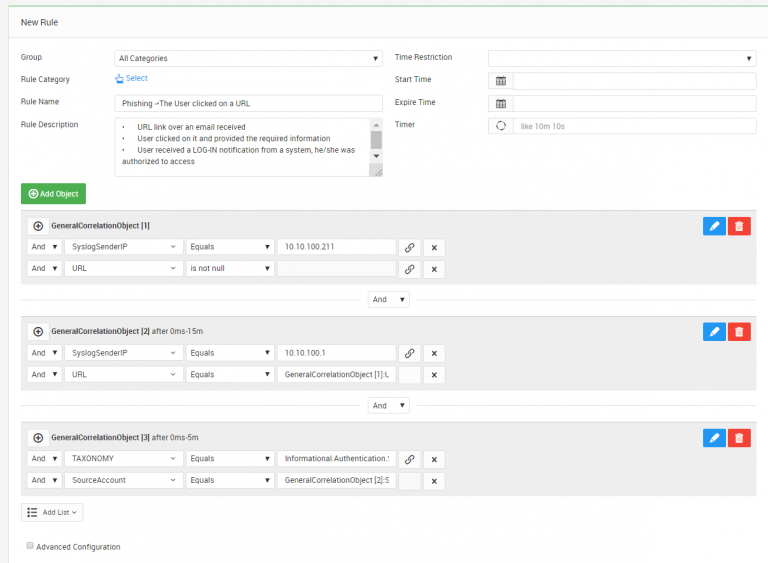
Rule Description
The first part of the rule [GeneralCorrelationObject [1]] collects log from mail gateway(sandbox). The IP of this log source is 10.10.100.211 and checks if the log contains any URL address.
The second part of the rule [GeneralCorrelationObject [2]] collects log from proxy or UTM. The IP of this log source is 10.10.100.1. This part of the rule checks if the logs contain any URL address which was detected on mail gateway logs before.
The third part of the rule [GeneralCorrelationObject [3]] collects log from all the log sources and checks if there is any authentication with the same user.
