LOGTITAN Taxonomy Features
Why is Taxonomy important? And Extensive LOGTITAN SIEM Taxonomy Features:
How come LOGTITAN detects things like a failed login from all brands and types of devices. The answer is in the taxonomy it uses.
A taxonomy aids in pattern recognition and also improves the scope and stability of correlation rules. When events from heterogeneous sources are normalized they can be analyzed by a smaller number of correlation rules, which reduces deployment and support labor. In addition, normalized events are easier to work with when developing reports and dashboards
Using normalized events and taxonomy categories is highly recommended in correlation because they make the rule easier to modify, maintain and apply to additional log sources.
With the ability to translates all log types into a single taxonomy, Sureog provides immediate time-to-value in the application of SIEM, meaning customers are empowered to build, manage and effectively transform their businesses through a unified cybersecurity solution
Taxonomy or event categorization is common in SIEM solution. The question is how strong, deep and powerful is your SIEM taxonomy capability?
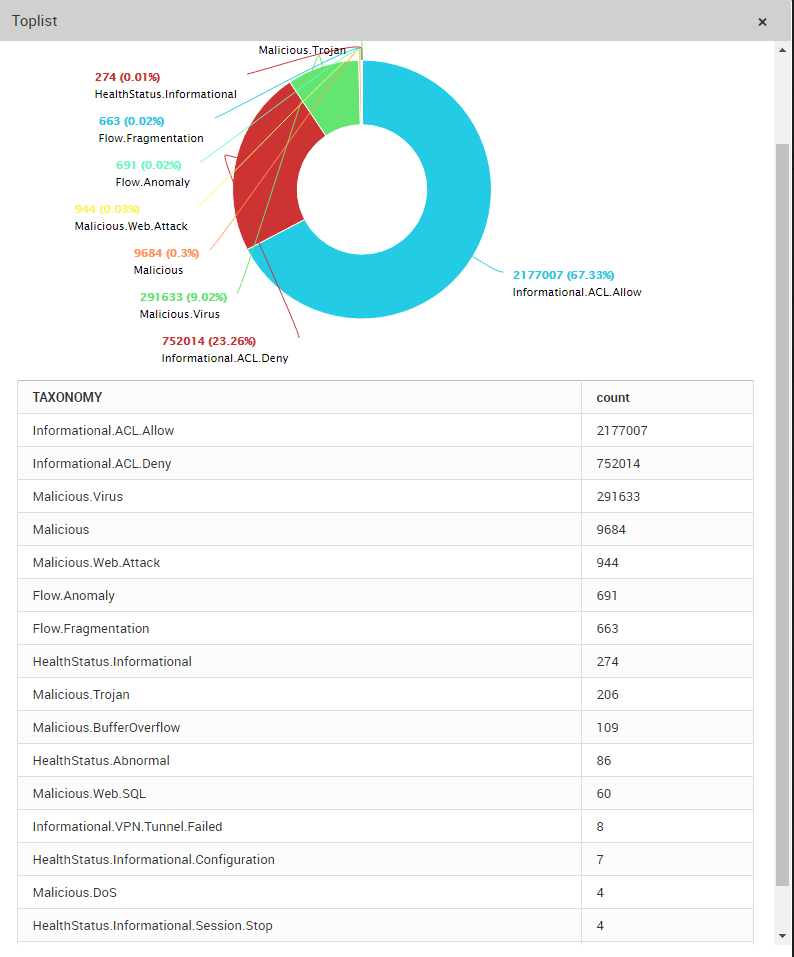
Sample LOGTITAN Taxonomy List
Almost all SIEM solutions have taxonomies for:
Successful Login
Failed Login
User Logoff
File Access
Firewall Drop
Firewall Accept
Process Start
Process Stop
System Reboot
SystemScanStart
System Scan Stop
System Shut down
Web Access
Session Start
Session Stop
User Created
User Deleted
Delete Group
Delete Domain Member
Password changed
Account Modified
Account Expired
Attack
Malicious
VPN connected
VPN Disconnected
But LOGTITAN has thousands of more taxonomies like :
Mail Service Access
Mail Service Denial
Mail Spam Denial
ICMP CODE Destination Network Unknown
Machine Auth Ticket
Machine Logoff
Machine Logon
ICMP CODE Alternate Address for Host
Multicast Router Advertisement
ICMP CODE Destination Unreachable for Service
ICMP CODE Destination is Administratively Prohibited
WebTrafficAudit->Adware
VirusTrafficAccess->Web Content
VirusTrafficAccess->Adware
FileTransferTrafficAudit->Adware
NamingTrafficAudit->Zone Transfer
UnusualUDPTraffic->ICMP IPv6 Where-are-you
UnusualUDPTraffic
UnusualTCPTraffic
ApplicationTrafficAudit->Access Denied
WebTrafficAudit->Header Malformed
PingOfDeathDenial
LandAttackDenial
LinkControlAccess
LinkControlDenial
LinkControlTrafficAudit
MachineAuthAudit
MachineLogonFailure
MachineModifyAttribute
MachineModifyPrivileges
UnusualICMPTraffic->ICMP Echo Reply
UnusualICMPTraffic->ICMP Unassigned
UnusualICMPTraffic->ICMP Host Unreachable
UnusualICMPTraffic->ICMP Source Quench
UnusualICMPTraffic->ICMP Redirect
UnusualICMPTraffic->ICMP Alternate Host Address
UnusualICMPTraffic->ICMP Echo Request
UnusualICMPTraffic->ICMP Router Advertisement
UnusualICMPTraffic->ICMP Router Selection
UnusualICMPTraffic->ICMP Time Exceeded
UnusualICMPTraffic->ICMP Parameter Problem
More than 1000 taxonomies.
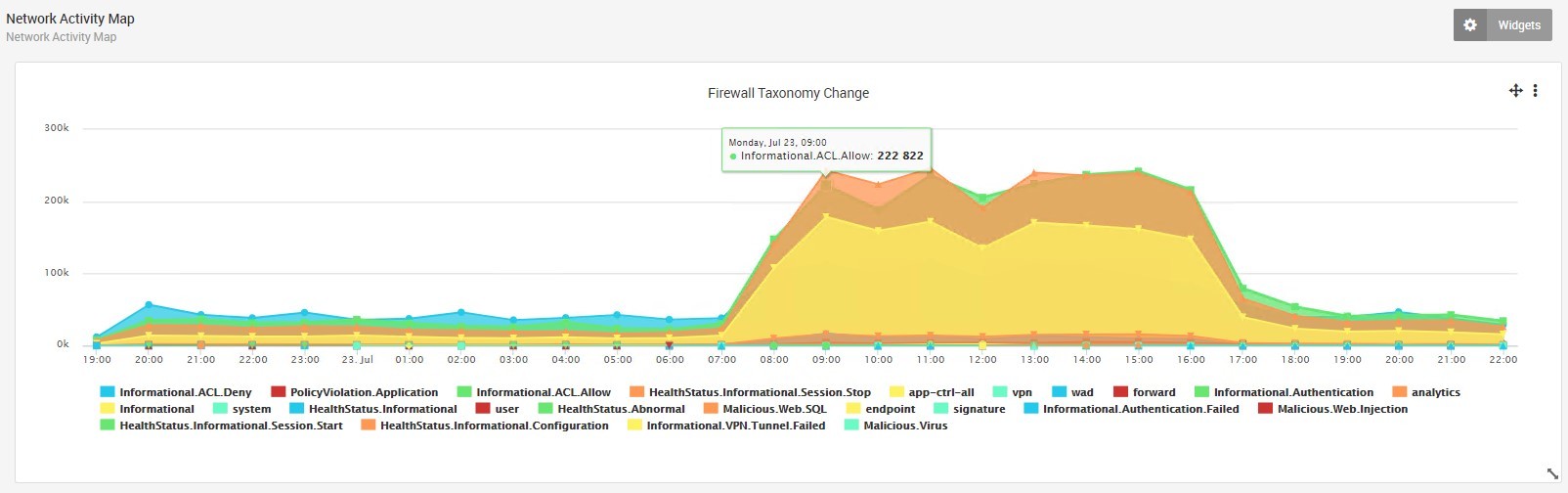
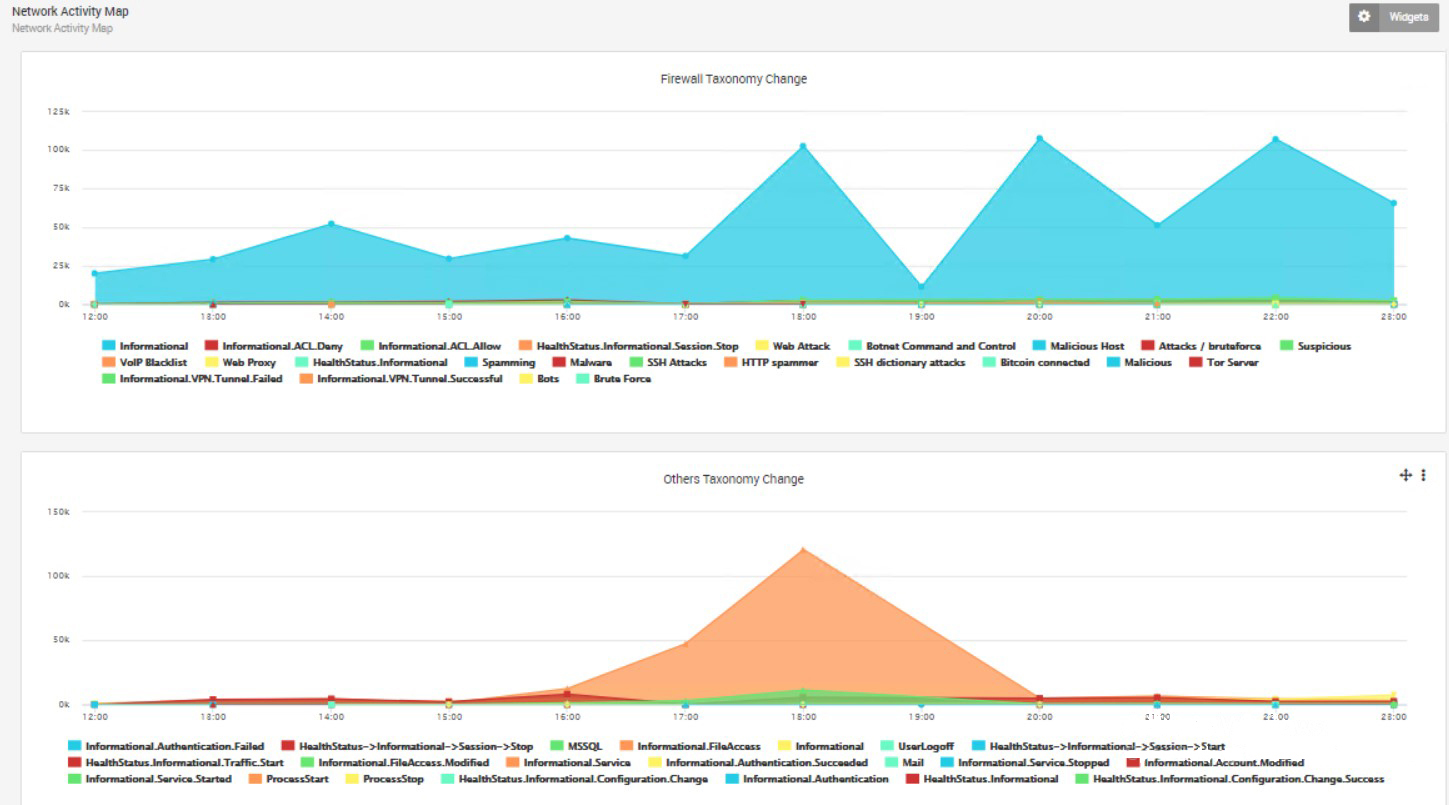
Taxonomy Trends
