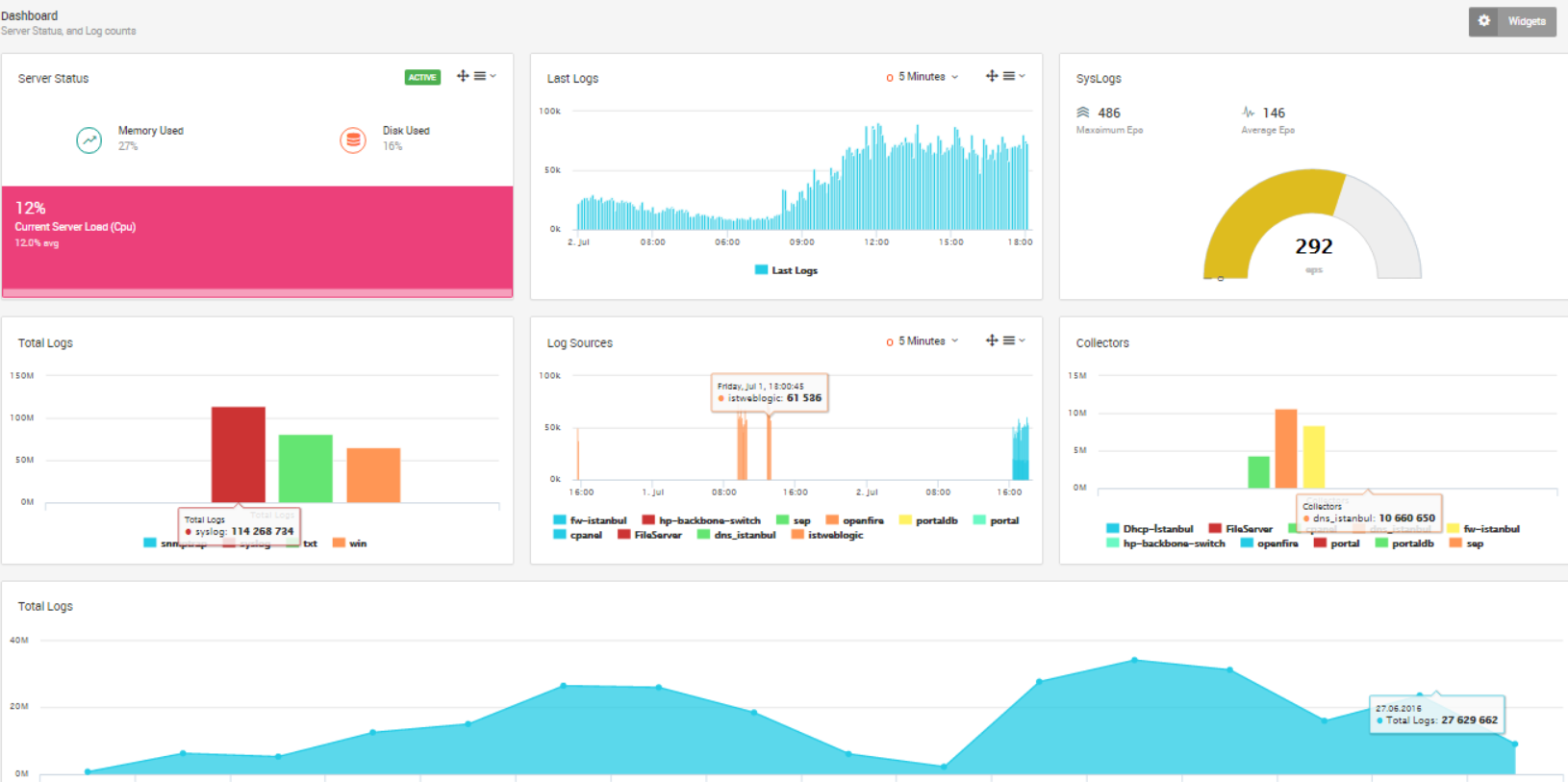
LOGTITAN SIEM.
Automate the monitoring process for resource-constrained security experts with LOGTITAN.
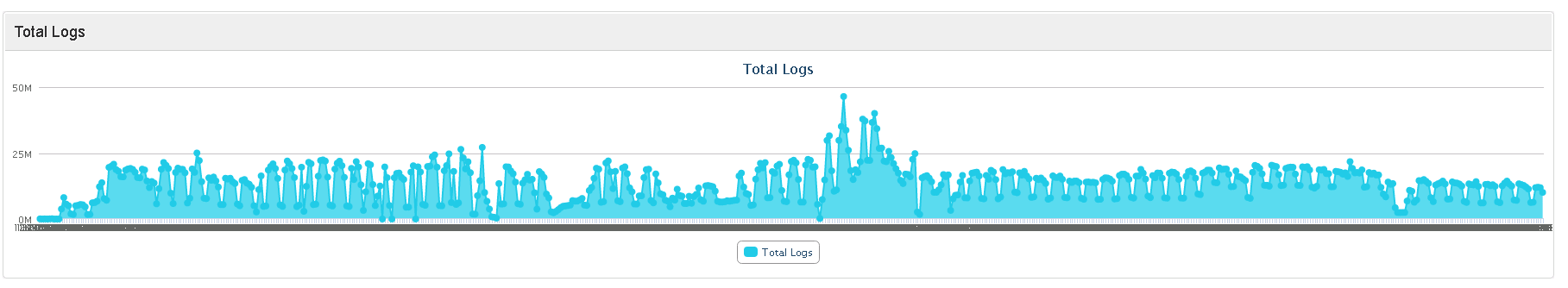
Security experts can’t stop what they can’t see. But without the people to actively monitor security activity, visibility is limited. Logtitan was specifically designed to address the monitoring needs of small security staffs. Logtitan delivers increased security visibility and reduced time-to-respond duration without needing additional headcount.
LOGTITAN BENEFITS.

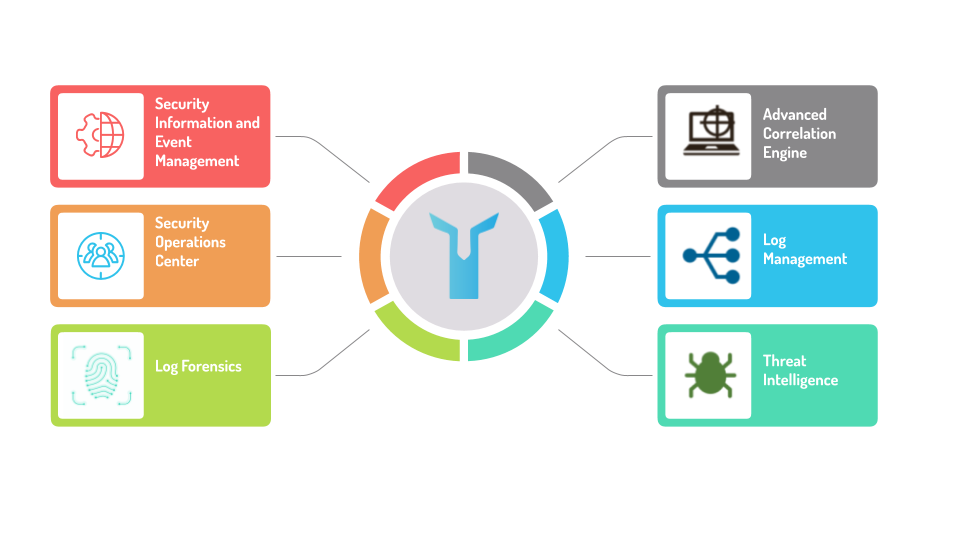
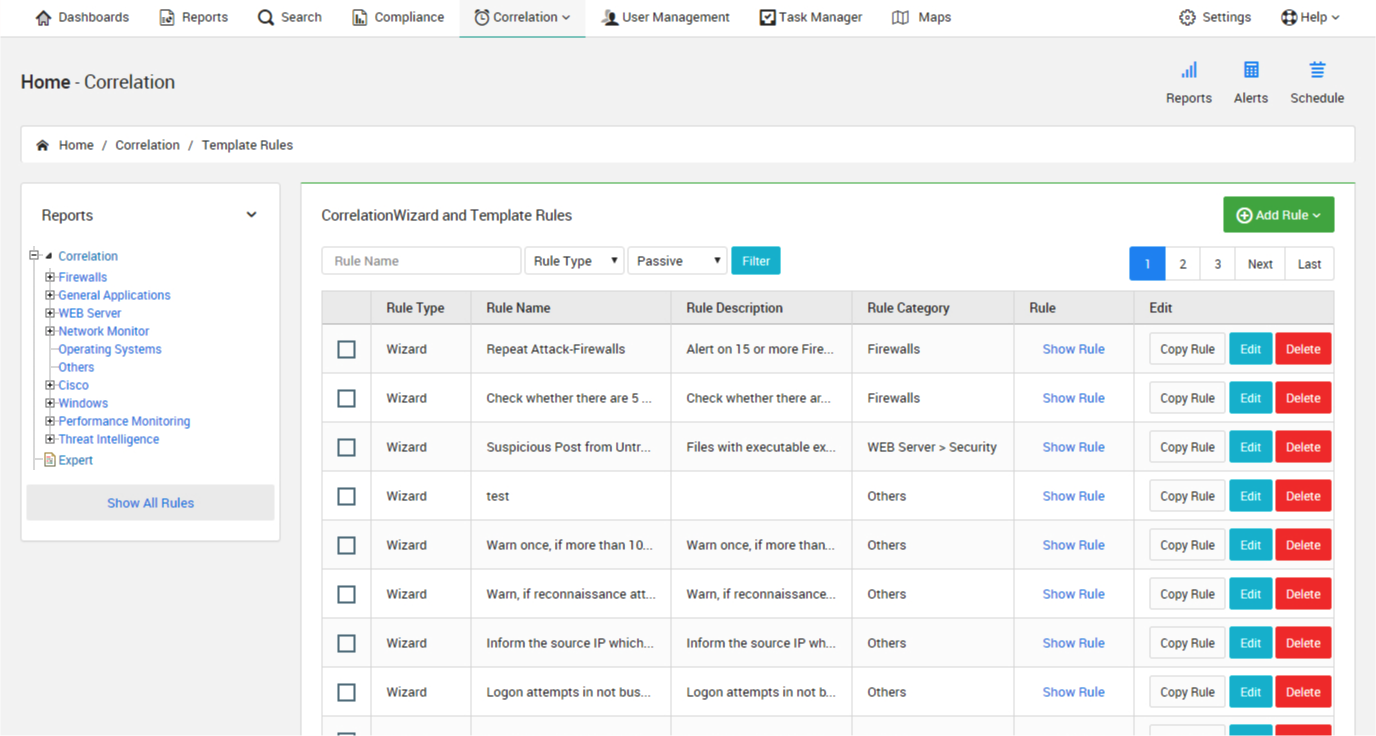
Superior Correlation Engine: Support developing complex rules with easy correlation rule editor.
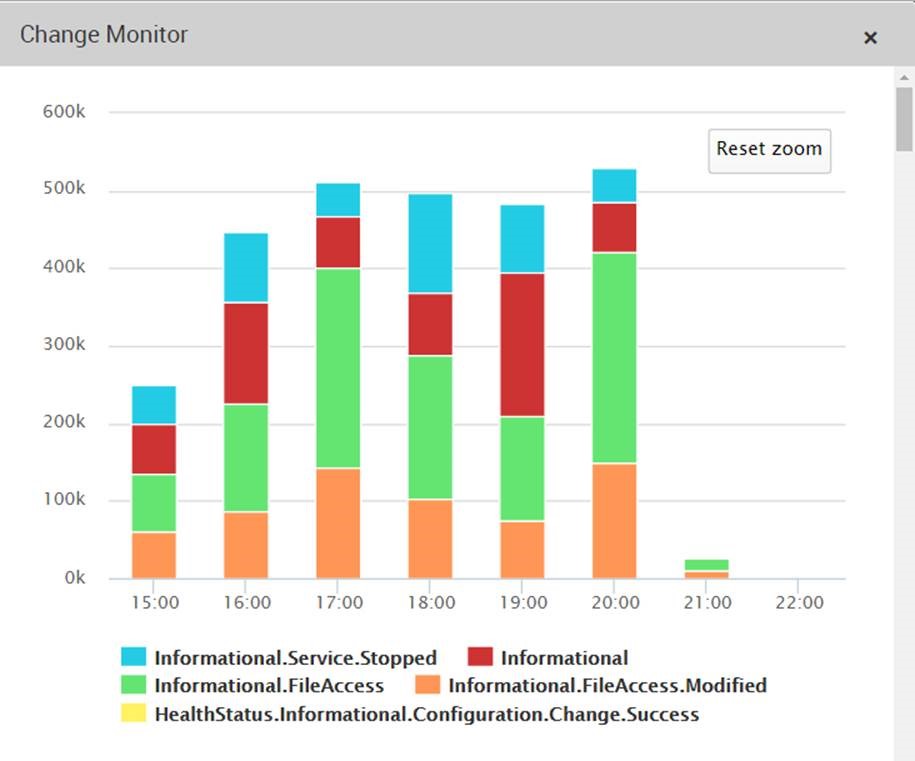
Integrated Security & Traffic Monitoring and Reporting.
LOGTITAN delivers security and compliance to organizations of all sizes.

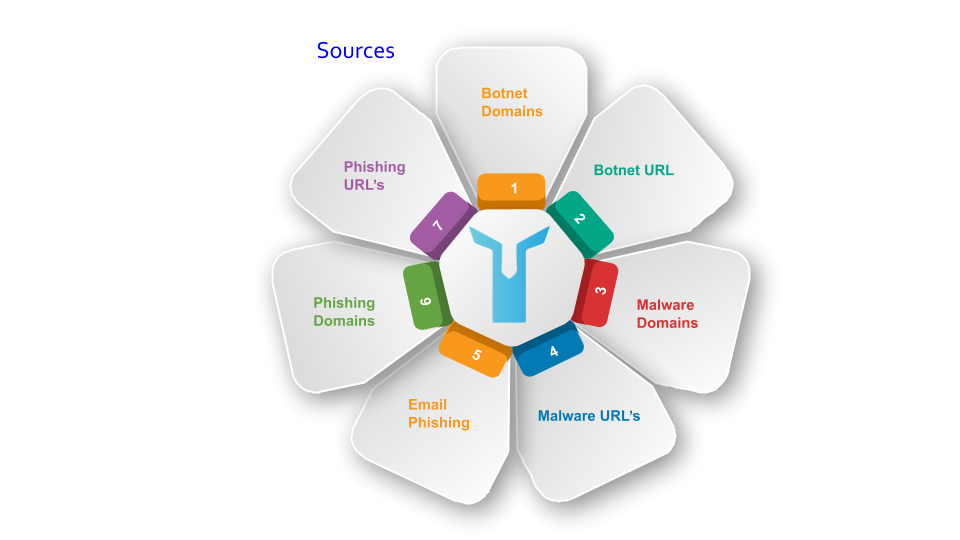
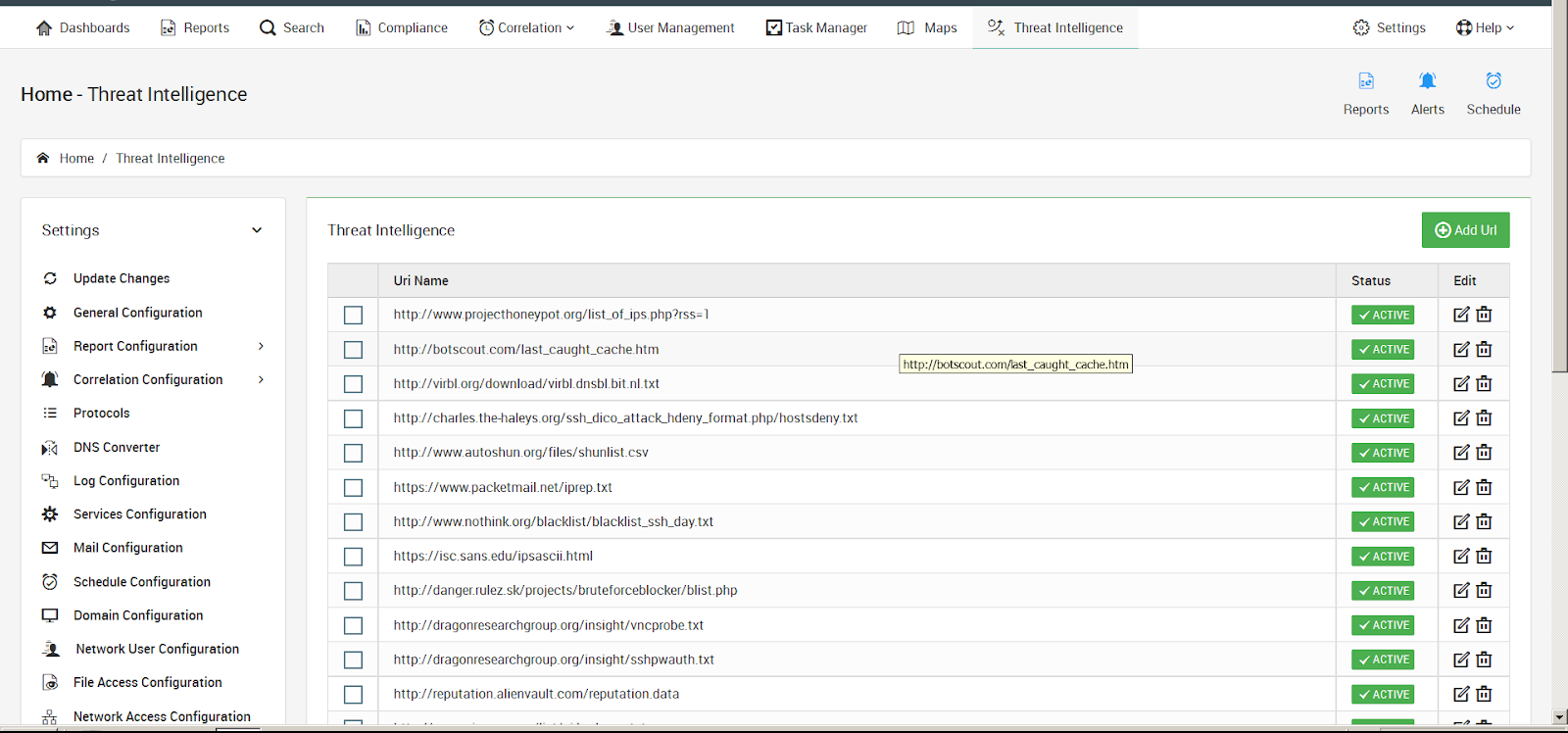
Sophisticated threat intelligence management allows LOGTITAN to dynamically collect black lists and update its database.
-
LOGTITAN aggregates more than 1 million threat information from numerous sources and applies automated confidence algorithms to produce intelligence and reputation data.
-
A large library of openly available information lists, which is consolidated, classified and automatically analyzed to derive intelligence and reputation information with confidence.
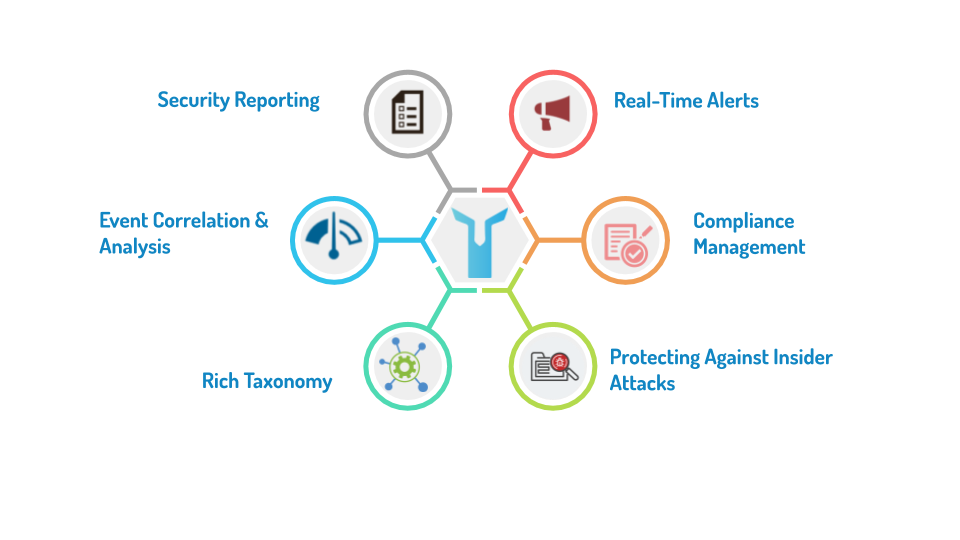
CORRELATION ENGINE
-
Leverages predefined rules to identify attack patterns and malicious behavior.
-
Automates analysis so that attacks can be quickly identified and breaches can be immediately contained.
CORRELATION ENGINE ADVANTAGES
LOGTITAN is fast.
LOGTITAN can trace multiple logs with different types within a defined time frame.
LOGTITAN can correlate different logs.
LOGTITAN can correlate privileged user behavior with specific network activity.
LOGTITAN can audit privileged user activity.
LOGTITAN supports multiple filtering options.
Compression-based correlation feature.
Correlation rule editor is simple to use.
LOGTITAN can trace a log being created with desired parameters or not.
TAXONOMY.
Mapping of information from heterogeneous sources to a common classification. A taxonomy aids in pattern recognition and also improves the scope and stability of correlation rules.
- Compromised->RemoteControlApp->Response
- HealthStatus->Informational->HighAvailability->- LinkStatus->Down
- IPTrafficAudit->IP Too many fragments
- PSpoofAccess->ICMP CODE Redirect for the Host
- FileTransferTrafficAudit->Authentication Failed
- NamingTrafficAudit
- Session->Start
- ICMP Destination Network is Administratively Prohibited